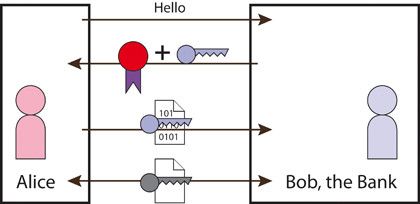
Security¶
I believe that good security is as simple as possible, so that requirements which are necessary to maintain it are understandable. The IOCOM security doesn’t answer device security as whole, only to communication security.
Contents:
updated 15.3.2021/pekka